Insight on Program Best Practices
How Proactive Investigations Can Boost the Bottom Line
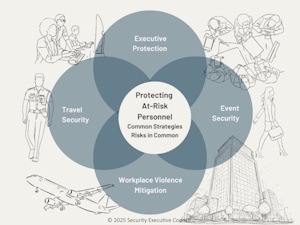
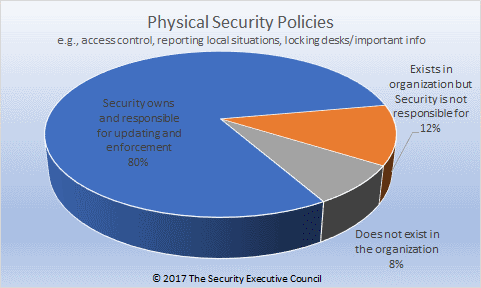
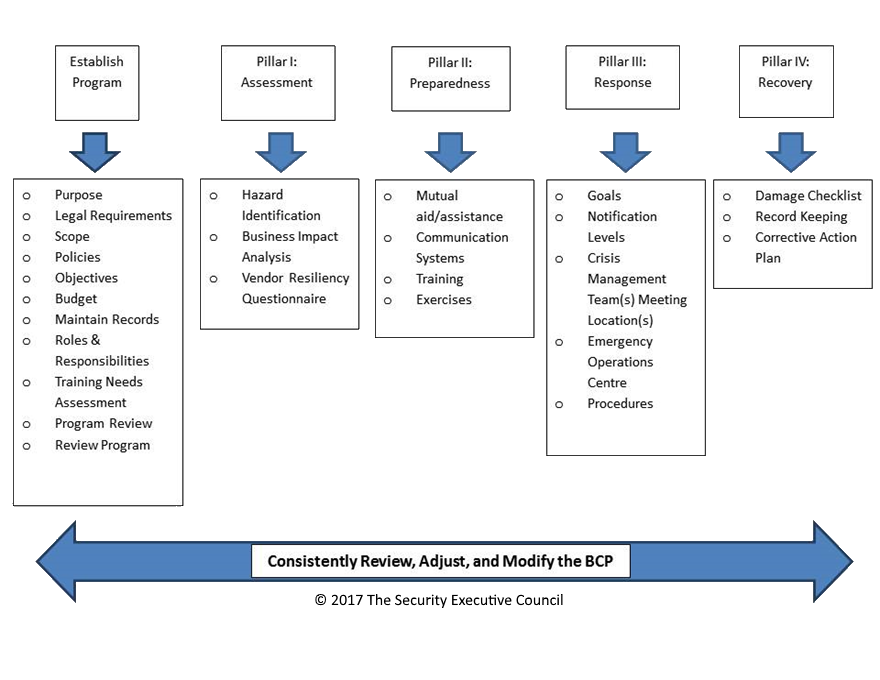
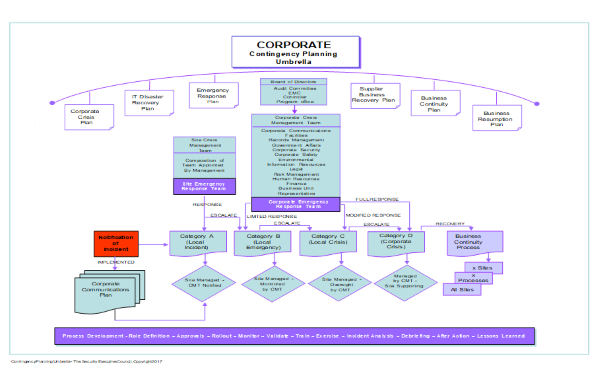
Organizations can incur criminal loss through many avenues – organized crime, theft and diversion, intellectual property loss, myriad types of internal and external fraud involving insurance, employee benefits, misappropriation, kickbacks, and more. Each of these loss avenues may be managed by a different function in the company, which is why...