Created by the Security Executive CouncilDefinition
Establishing an insider threat program begins with agreeing to a definition and scope that works within your organization. However, to be effective, an insider threat program must consider the expansive universe of actors that can make up the set of "insiders". Contractors and vendors that are provided access to your facilities or systems should be included.
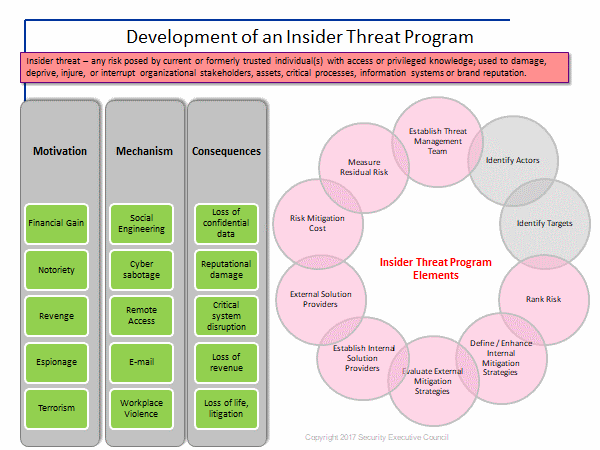
Program Elements
A list of insider threat program elements can be beneficial when building a program or reviewing an existing program. Here are some elements to give some thought to:
- Identify actors
- Identify targets
- Rank risk
- Define / enhance internal mitigation strategies
- Evaluate external mitigation strategies
- Establish internal solution providers
- Establish external solution providers
- Identify risk mitigation costs
- Measure residual risk
- Establish a threat management team
Motivation – Mechanism – Consequences
The three pillars of any action are; 1) the motivation or reason driving the action; 2) the mechanism or method used to carry out the action; and 3) the result or consequences of taking that action. Identifying and analyzing insider threats suggests the need to examine these three pillars when executing on the risk management process.
Valuable Tools
The following chart can be used to help keep these important factors in mind when building insider threat programs. You can download a PDF of this chart below. Keep it handy for working on your program.