Created by George Campbell, Security Executive Council Emeritus Faculty member.
Introduction. The delivery of excellence in a business’ products or services has always been a widely accepted objective. But expectations took on a more formalized agenda in the 1980s, culminating with the Baldridge National Quality Award and the Shingo Prize, which became standards of excellence for business. Global competition in manufacturing spawned several disciplines targeting continuous improvement, defect elimination, cost management, supply chain efficiency and the customer/value relationship. In sum, these and their companions in the pursuit of quality-driven operational performance can all be placed in a bucket labeled “Business Excellence.” If enterprise security is to be effectively aligned with its company’s strategy and processes, it must be driving a focus on operations excellence (OpEx) into every corner of its suite of products and services.
Objective. The Security Executive Council has several Tier 1 Security Leader™ members who have assigned senior staff resources to the development of programs calculated to drive OpEx into their security operations. Some of these executives are in industrial sectors with established processes like Kaizen and Six Sigma, while others seek to explore the results that these proven quality management practices offer. This short review seeks to explore an approach to support those leaders and to inform others who may be interested.
Initial Member Feedback. We conducted brief interviews with several interested members to document organizational context, obtain a working definition of the process they envisioned for their security operations, and gauge their interest in establishing a group effort to share learning and push ideas. Their feedback is summarized below.
- Business excellence is ingrained in our company’s processes and we need to be aligned with this way of managing performance.
- I know there are a variety of standards to benchmark, but I think operational excellence is about exceeding those standards.
- Operational excellence is about security process transformation.
- The ideal outcome of an OpEx working group would be the creation of a security manager’s operational excellence toolkit.
- There is a critical need for security to communicate its value—demonstrating excellence in service is a driver of that communication strategy.
- Relationship between governance and operational excellence—how are we performing in our relationship to the policy infrastructure?
- We should do OpEx benchmarking and exchange ideas across security organizations in companies engaged in these disciplines.
- How can we measure the effectiveness of security programs to business outcomes?
- Explore the opportunity to deep dive on a core security process to examine how excellence is or could be demonstrated.
- We need to understand how operational excellence is made part of business process and how this has influenced corporate security’s engagement.
There was agreement that the group could fairly easily "get into the weeds" and miss the big picture. Participants acknowledged a need to find an approach to discussions that would help build real, actionable tools. These practitioners are too busy for academic discussions that don’t contribute to something useful in security practice management.
Conclusions. There were a few key conclusions from these discussions, none of which should be surprising to experienced security practitioners.
- Each company is approaching this initiative from its own unique organizational framework around the subject and its own equally unique enterprise risk framework.
- There are marked differences in maturity and focus of approach. Some seek a highly limited application while others seek to apply this across the suite of security services.
- There is no shared definition of excellence, quality or other key performance measures that would facilitate common benchmarks. (IT security is a notable exception. The Council can provide multiple examples in other areas of security program management but they may not be universally applicable or supportable.)
Implications for building a model approach.This document reflects these conclusions and attempts to establish a foundation from which we may attempt to engage interested parties in a structured approach to operations excellence, at least at a trial level. In practice, the various disciplines are so specifically defined that it seems logical to build a model that encompasses a generic process that could feed into more or less mature approaches.
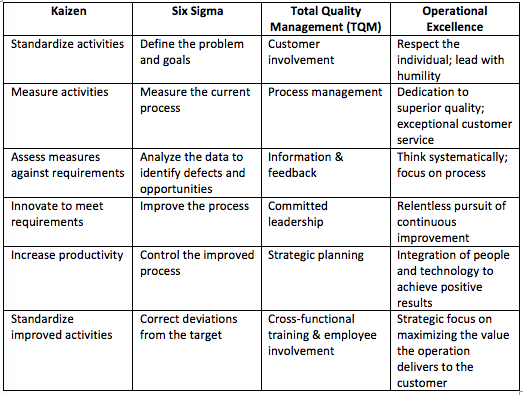
The Process Landscape. Even the most cursory review of the literature reveals the potential appeal to those who find this focus on business excellence enticing. Consider the following table that summarizes key elements of four of the frameworks that may be applied. (There are other disciplines that could be included, but these few appear to contain the common process components.) Note the consistent themes of requirements analysis, innovation, process improvement, quality management, leadership and team involvement, measurement, and a total engagement with the customer. All of these are obvious program management objectives. But as we launch a more defined and deeper dive into individual security tasks wherein we seek measurably improved service levels and outcomes, we need a significantly more structured plan of attack.
 Setting the Stage:
Setting the Stage: Security’s Balanced Scorecard. The balanced scorecard was introduced in 1992 by Kaplan and Norton in a Harvard Business Review article. The authors believed that the excessive use of financial scorecards in business failed to encompass the full scope of performance measurement. For our purposes, the four perspectives they introduced are seen here along with a translation that emphasizes the connection to our security mission.
- Financial Perspective: How do we look to shareholders? What capabilities, goals & measurements in our safeguards are perceptible to shareholders?
- Internal Business Perspective: What should we excel at? What elements of our key protection programs demonstrate best-in-class practices?
- Innovation and Learning Perspective: What security goals, activities and measures are calculated to improve security at reduced or avoided cost and thereby add value?
- Customer Perspective: How do customers see us? What specific security programs and activities visibly contribute to our customers’ satisfaction and measurably add value for them?
These four perspectives effectively summarize the concepts in the various business excellence disciplines noted above. Importantly, they provide a significantly more comprehensive view of an organization’s performance and, in this framework, force a critical assessment of security’s value. Answering these few questions can kick start the quest for excellence in enterprise security.
Then, we can follow up with another series of questions that can help establish a baseline for our specific approach to security excellence.
What is “excellence”? As professionals, we can all agree that achieving excellence in our work is our goal. And it goes without saying that excellence is an expectation of those we serve. But how should we—our stakeholders and ourselves—define excellence in our suite of services? Is it in the quality of security program results and, if so, where are the established standards to measure a requisite degree of quality? At the end of the day, customers define quality and value. The “owner” of the security process cannot be the sole arbiter of its level of quality and excellence. But the security function is also not the sole contributor to a secure business process. Security is a shared accountability with degrees of contribution linked to the requirements of protection. Clearly, engaging stakeholders and customers in analysis of our activities is an essential ingredient in the process. Our customers do not typically understand security activities, and a well-planned examination of what service excellence means to them will make activity analysis and measurement more effective and more valuable.
Is the security program effectively aligned with its customers? Every business excellence discipline shares a singular focus on the customer. Ask every member of the security team, “Who is your customer?” This may be a multiple choice question:
- Is it the employee seeking our assistance or expecting a safe and secure place to work?
- Is it the business unit owner of a risky process?
- Is it the CEO who expects us to deliver the promised results?
- Is it the Board or the shareholders who need to know that risk is being managed?
- Or is it the external customer who may be served by a corporate commitment to security and integrity in products and services?
It’s likely that all of these are Security’s customers. Each group likely brings its own definition of excellence and perception of value. And few or none of these have the requisite information to know the intricacies of what we do. But whoever the customer is for a given transaction, he or she has a critical opinion of the quality and responsiveness of what you have delivered and whether it is worth the price. Therein lies the challenge in this process of analyzing, defining and delivering excellence through best-in-class security services.
Is a “best practice” equal to excellence in that practice? Where a security practice can be shown to deliver results consistently superior to an alternative process that has been applied and tested by others, it should be advertised as having achieved a level of excellence. The key is measuring the “superior results,” and that requires detailed task and process analyses, which are consistent elements in virtually all business excellence disciplines.
What is the relationship of risk management to operations excellence? The presence of risk is the business driver for the security program. Excellence in our business mission has to link to a positive impact of security activities on the reduction of targeted risk. If our security activity was the singular source of identification and proven elimination of an exploitable vulnerability, would that activity be accurately labeled as having achieved excellence? If I can demonstrate the business impact of adversary exploitation of that vulnerability, have I demonstrated measurable value? It may be said that excellence in security operations cannot be achieved without a robust process of security risk assessment that results in the measurable elimination of business process vulnerabilities.
Where is value in the excellence equation? Defining the value proposition for our services is a primary objective of an exercise in operations excellence. We seek to document the sum total of the benefits the customer, the stakeholder or the enterprise will receive from the security service we offer. When we can define a level of performance that delivers a measurable benefit (like less risk or faster, better response), we have the ability to not only improve performance but to positively influence the perception of value by key constituencies or stakeholders.
If a security process or activity lacks established performance measures, can excellence be achieved in that process or activity? It is not possible to establish that a security process has achieved excellence or provided value if relevant performance measures have not been vetted and consistently applied.
Probing Potential Measures of Excellence in Security Programs. What statements might sufficiently convey a demonstration of excellence in security programs? Consider the following:
- A security program demonstrates such effective alignment and contribution to the success of a business process that it measurably enables the business to do what would otherwise be too risky or non-competitive. Moreover, business is captured and/or retained solely due to the quality of security measures proposed or applied.
- Measurable capabilities in safe & secure workplace protection result in increased productivity, lower insurance cost, increased worker morale and reduced incidence of injury and fatality.
- A security activity is peer-reviewed or benchmarked against available standards or best practices and exceeds qualitative measures of performance. Certain control factors being equal, losses attributable to security breach are measurably less (over time) than industry sector peers.
- The cost of a secure business process or environment is less than the consequences of risk or, the cost is additive but those at risk feel measurably safer and more productive. Or, an incremental increase in asset protection is achieved at reduced cost to the customer.
- A customer’s expectation (or service level agreement) is consistently and measurably exceeded
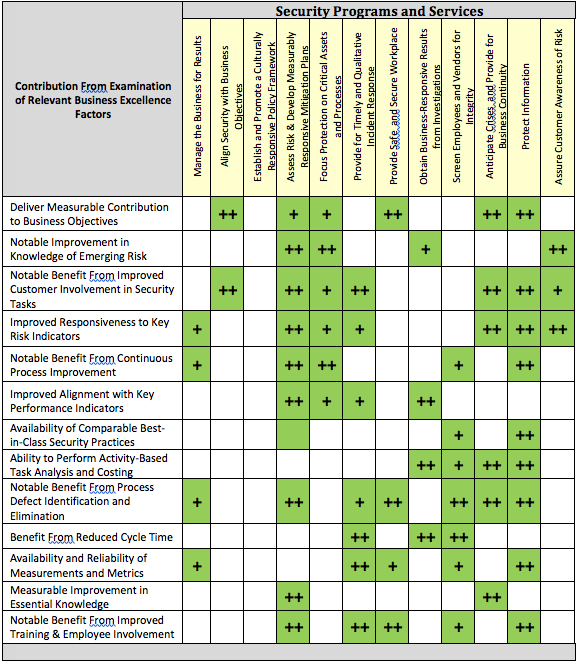
Target Analysis: A Business Excellence Template. If a process has not already been identified for analysis and application within your company, you may want to consider the following table as a team exercise. Several components in the disciplines noted above, along with a few others that are appropriate, have been incorporated under Business Excellence Factors. Each of the Security Programs and Services may be discussed, evaluated and selected for the potential benefits that may accrue as a result of an in-depth application of an operations excellence approach.
For the purposes of this paper, several items in the table have been highlighted and noted (+/++)
1 where an added benefit may be found through subsequent analysis. (You could probably color every box in green, but this seeks to call out the most obvious.) The idea is to think through how each of the possible benefits on the left may impact and deliver measurable results to the security service targeted. This is only an example of how this matrix may be used; a blank table is offered in the appendix.
1 A scoring routine might enable a more granular assessment. Score 1 for low benefit and up to 5 for an almost guaranteed improvement
 Next Steps: Building a Business Excellence Toolkit.
Next Steps: Building a Business Excellence Toolkit. The fact that OpEx is only now gaining some traction in security management circles speaks volumes about our level of alignment with several decades of established business excellence and quality programs across technology, manufacturing and service industries. We have interest from several member organizations and an opportunity to initiate a movement that is overdue in our profession.
What is necessary now is to engage organizational leaders, find answers to the questions we have raised in this paper, and develop a body of practical tools and techniques that may be applied across a wide range of corporate security programs. There is no “one size fits all” in corporate security functions or in the diversity of business missions and models they serve. But we do believe we can collectively put forth a body of workable definitions for various security activities, provide measures and metrics appropriate to assessing performance and service quality and craft tools and templates that will support the pursuit of documented excellence.
Suggested Reading. There are scores of books and reams of Internet data on the business excellence subject. For an outstanding summary, check out Back to Basics: A Practitioner’s Guide to Operations Excellence by Douglas Sutton, Operations Excellence Services, LLC (2012). For tools and techniques: The Lean Six Sigma Pocket Toolbook, Michael George, McGraw Hill (2005); Balanced Scorecards and Operational Dashboards with Microsoft Excel, Ron Person, Wiley Publishing (2009); “Shingo Prize Model and Guidelines,” Jon Huntsman School of Business, Utah State University,
www.shingo.org.
Appendix: Business Excellence Analysis Template